BGProtect
Protecting the Internet’s Core Infrastructure
Of Software Agents
Network Data
Database
BGProtect provides Cybersecurity Solutions for threats arising from network vulnerabilities:
BGP Hijacking
Real-time monitoring and alerting for BGP hijacks and route leaks.
DNS Poisoning
Comprehensive protection against DNS amplification attacks and cache poisoning.
Threat Intelligence
Existing custom solution for predictive threat intelligence.
Custom Solutions
Tailored security and monitoring packages for unique critical infrastructure requirements.
Trusted by Global Leaders
Fortune 500
Securing complex global enterprise networks and data centers.
Financial Institutions
Protecting banking cores and high-frequency trading infrastructure.
Critical Infrastructure
Trusted by Leading Government Cyber Defense Agencies.
Defense Rooted in
Academic Rigor
BGProtect is the commercialization of three decades of internet measurement research.
From pioneering distributed network mapping with the
DIMES Project, to defining BGP hijack detection standards using AI,
our methodology is peer-reviewed and battle-tested.

Prof. Yuval Shavitt
Co-Founder & CTO
Tel Aviv University • IEEE Senior Member
Yuval Shavitt and Omer Shraibstein
Non-Standard Large TTLs in DNS Query Responses
"Investigating the prevalence and security implications of anomalous Time-To-Live values within the global DNS ecosystem."
Chris C. Demchak and Yuval Shavitt
China’s Maxim – Leave No Access Point Unexploited
"The definitive analysis of China Telecom’s BGP hijacking strategy. Recognized as MCA's most popular paper (over 95,000 downloads)"
Alex Maltinsky, Ran Giladi, Yuval Shavitt
On Network Neutrality Measurements
"Exploration and methodology for detecting network neutrality violations through active measurement."
Yuval Shavitt and Eran Shir
DIMES: Let the Internet Measure Itself
"The foundational distributed measurement infrastructure that pioneered modern internet topology mapping."
Latest Insights

China's Maxim: BGProtect's Role in Shaping US Cyber Policy Recommendations
How specific BGP hijacking maneuvers reshaped US Cyber Policy and exposed the fragility of the global internet.
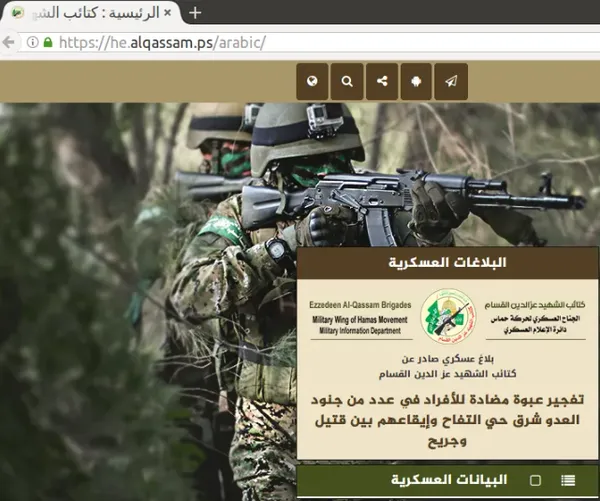
Al-Qassam’s Global Hosting Network: Reliance on Global Infrastructure
Our latest intel reveals how Hamas’s military wing maintains a web presence via a complex chain of Iranian, Ukrainian, and British infrastructure.
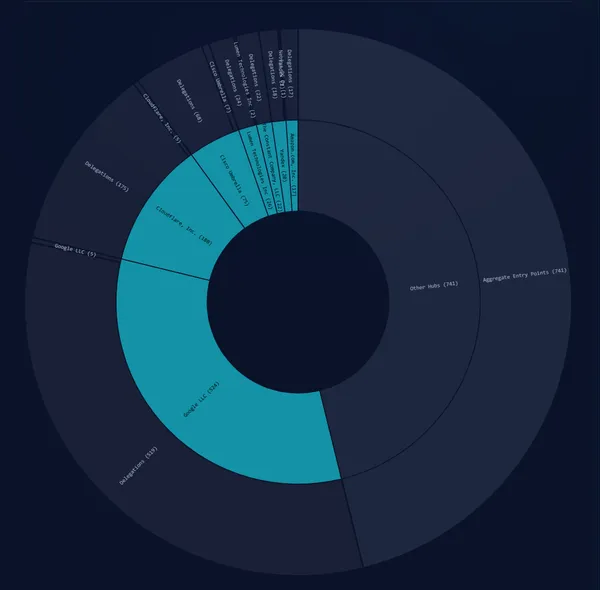
The Hidden Centrality of DNS: How Independent Resolvers Delegate to the Few
While the DNS ecosystem appears decentralized, our data reveals a significant concentration of dependency on a small number of public resolvers.